In today’s time applications and data is rapidly been shifted on the cloud and cloud computing technology is improving day by day. But more the functionality is increased the more cloud security challenges are faced by companies.
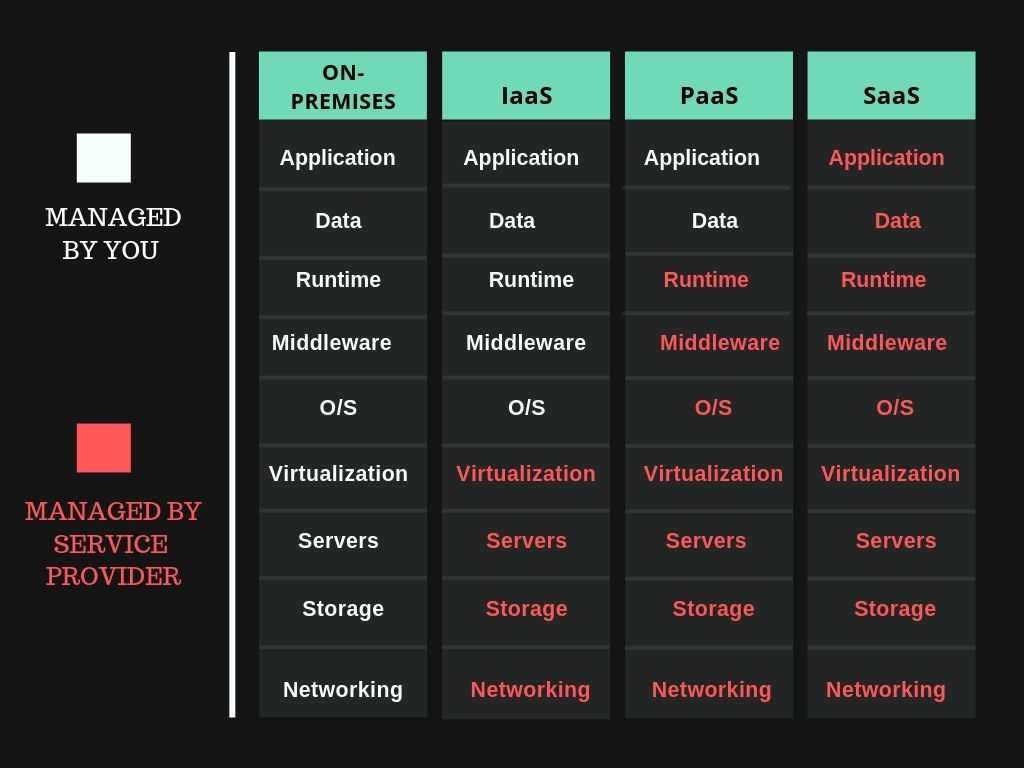
It is very important in today’s time as data is our primary concern. There are various security risks of cloud computing, Therefore there are various cloud computing service models.
- On-premises (own server)
- IaaS (Infrastructure as a Service)
- SaaS (Software as a Service)
- PaaS (Platform as a Service)
5 Most important cloud security challenges associated with service models are:-
1. Insufficient Identity, Credential, and Access Management:- Lack of Identity Access Management can lead to the user performing activity which is outside their scope of authority.
How to implement proper IAM?
- Secure accounts with two-factor authentication and limit the use of root access to the account.
- Implement strict identity and access controls for cloud users.
- Enable the use of custom keys for secure authentication.
- Rotate keys, revoke unnecessary privileges.
2. Data Breaches:- Data breaches happen at the time of cyberattack. confidential, sensitive information of the customer is accessed or disclosed in an unauthorized fashion.
How to prevent data security breaches?
- Audit domains.
- Monitor traffic.
- Give only necessary access to users.
- Use some encryption techniques (drawback: application gets less user-friendly)
- Get a team to implement an advance incident response plan for recovery.
3. Account Hijacking:- Attacker get hold of someone else’s account on the cloud to do malicious activities. Most of the attacker uses a compromised email account or other credentials to impersonate the account owner.
How to prevent account hijacking?
- Enable background checks for employee accessing servers in data centers physically.
- Implement a strong policy for authentication for cloud app users.
- IAM control policy is key in preventing account hijacking.
- Make sure all of your data is securely backed up with cloud backup services.
- Allow specific IP addresses to access cloud applications. Some cloud apps also provide tools to specify allowable IP ranges.
- Enable multi-factor authentication.
- Encrypt sensitive data before sending to the cloud.
4. Insecure APIs:- API is an application program interface which enables two applications to communicate. These interfaces should be strong enough that they would not become a bottleneck for availability, confidentiality, integrity, and security of systems and data.
How to prevent from insecure API?
- Security audits and cloud testings on a regular basis
- use protected API keys and make sure it doesn’t get reused.
- Considerations for effective API designs and Pick the right cloud provider API.
- Use TLS for all data exchanges.
5. DoS and DDoS attack:- These are both denial of service attacks, attackers do so that the server cannot respond to legitimate requests. Attack done by the single system is DoS, and if done in a distributed way is DDoS attack.
How to prevent DDoS and DoS attack?
- Do vulnerability Assessment and penetration testing to think and test like hackers.
- Deploy anti-DDoS hardware and software modules.
- Deploy a DDoS protection appliance with vendors like Cisco, NetScout, etc.
- Prevent DDoS Attacks on a Cloud Server using Open Source Softwares. like NGINX, Apache mod_evasive module, etc.
Top cloud service providers 2019
- Amazon Web services (visit: https://aws.amazon.com)
- Kamatera (visit: https://www.kamatera.com)
- Google Cloud platform (visit: https://cloud.google.com)
- Digital Ocean (visit: https://www.digitalocean.com)
- Microsoft azure (visit: https://azure.microsoft.com)
Top cloud security service providers 2019
- Sophos (visit: https://www.sophos.com/en-us.aspx)
- CipherCloud (visit: https://www.ciphercloud.com)
- Symantec (visit: https://www.symantec.com)
- Fortinet (visit: https://www.fortinet.com)
- Cisco Cloud (visit: https://www.cisco.com/c/en_in/products/security/cloud-security/index.html)
- Palo Alto Networks (visit: https://www.paloaltonetworks.com)