What is a Firewall?
A firewall is a network security device that looks after incoming and outgoing traffic. It is the device that gives access to incoming or outgoing traffic. It decides whether traffic will be allowed or not based on a set of rules which are predefined. Its purpose is to establish a barrier between your internal network and incoming traffic from external sources – such as the internet – in order to block malicious traffic like viruses and hackers.
Firewalls are present in both personal and enterprise settings. Many devices come with one built-in Firewall, including Mac, Windows, and Linux computers. These are essential components of network security. Firewalls are tools that can be used to enhance the security of computers connected to a network. They are an integral part of a comprehensive security framework for your network.
Why are Firewalls important?
Firewalls are important because they have a huge influence on modern security techniques. Firewalls have major use in the network security domain. As complexity in security methods increase, demand for firewalls also increased. Firewalls have since become the foundation of network security in the client-server model.
Firewalls are the architecture of networks in modern computing. Most devices use firewalls to inspect traffic and find threats such as viruses and worms.
What Firewalls do?
Firewalls perform various tasks to add extra layer of security in your network.
As your devices contain many resources. So we need a firewall to defend your resources from hackers. The firewall tracks the activity on incoming and outgoing data from the network. It validates access before entering into your device. The medium for entering your device here is the network. Firewall manages and controls network traffic very efficiently.
Firewalls record any malicious activity on the network. It creates reports on the recorded data and triggers to the user. It acts as intermediary between network and your device.
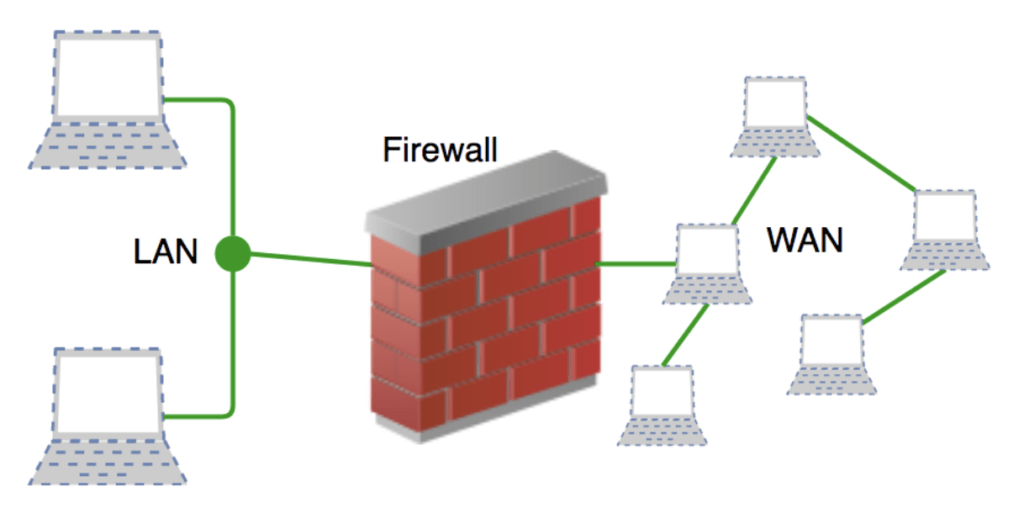
Where can you use Firewalls?
Firewalls have come in both corporate and consumer settings. Modern organizations incorporate them into a Security Information and Event Management (SIEM) strategy together with other cybersecurity devices. Basically, they are present at an organization’s network perimeter to guard against external threats or within the network to create segmentation and guard against insider threats.
In addition to immediate threat defense, firewalls act as important in logging and audit functions. They keep a record of events, which administrators use to identify patterns and improve rule sets. Updation of rules should be done on regular basis to keep up with ever-evolving cybersecurity threats. Security agents discover new threats and develop patches to cover them as soon as possible.
They are especially useful for always-on connections, like Digital Subscriber Line (DSL) or cable modem. It is important in these types of connections because those connection types use static IP addresses. They are often merging with antivirus applications. Personal firewalls, unlike corporate ones, are usually a single product as opposed to a collection of various products. They may be a device with firewall firmware. Hardware firewalls are for setting restrictions between in-home devices.
What is a personal Firewall?
A personal firewall is an application that controls network traffic to and from a computer, permitting or denying communications based on a security policy. Typically it works as an application layer firewall.
A personal firewall differs from a conventional firewall in terms of scale. They will usually protect only the computer on which it is installed, as compared to a conventional firewall. Conventional firewall a designated interface between two or more networks, such as a router or proxy server. Hence, personal firewalls allow security policy set for individual computers, whereas a conventional firewall controls the policy between the networks that it connects.
Why you need a personal Firewall?
At present times of high-speed internet access, when you are connected to a broad network you need to have a personal firewall. Without it, you may limit control and protection from the environment around you. Until recently, unless you worked for an organization that provided high-speed internet access.
Like anything, the high-speed connection has its own drawbacks. Ironically, the very feature that makes a high-speed connection attractive is also the reason that makes it vulnerable. In a way, connecting to the internet via high-speed connection is like leaving the front door of your house open and unlocked.
Because of high-speed internet, you may have certain features. A constant IP that makes it easy for an intruder who has discovered your computer on the internet to find you. Since you have constant IP he can find you again and again. High-Speed access tells that the intruder can work much faster when trying to get into your computer. Always active connection means that your computer is vulnerable every time when it is connected to the internet.
Importance of personal Firewall
- Most of the time you surf the internet, you are connected to a broadband connection. So there is a need for a personal firewall to provide protection.
- A personal firewall is necessary when you are using any public wi-fi network in places such as cafe or airport.
- Many times you run a home network that needs to isolate from the internet.
- You wish to be alert when any program on your computer attempts to connect to the internet.
- Most Personal Firewalls are highly configurable so you can easily create security policies to suit your individual needs.
How does a Firewall work?
A firewall establishes a border between an internal and external network. It is inserted inline across a network connection. It inspects all packets entering and leaving the guarded network. As it inspects, it uses a set of pre-configured rules to distinguish between malicious packets.
The term ‘packets’ refers to pieces of data that are available for internet transfer. Packets contain the data itself, as well as information about the data, such as where it came from. Firewalls can use this packet information to determine whether a given packet breach any of the rule set. If it does not, the packet will not get permission to enter the internal network.
Rule sets can be based on several things indicated by packet data, including the source address, the destination address, and the content of the packet.
Types of Firewalls
The above characteristics may represent differently at different levels of the network. As a packet travels through the network, it asks several times to tell the protocol where to send it. Different types of firewalls exist to read packets at different network levels. Firewalls are categorized by the way they filter data, or by the system they protect.
Packet Filtering Firewalls
Packet-filtering firewalls are the most common type of firewall that examine packets and prohibit them from passing through if they don’t match an established security ruleset. This type of firewall checks the packet’s source and destination IP addresses. If packets match those of an “allowed” rule on the firewall, then it trusts to enter the network.
When a packet passes through a packet-filtering firewall, it checks source and destination address, protocol, and destination port number. If the packet does not comply with the firewall’s rules, then the firewall drops it. For example, if a firewall configures with a rule to block Telnet access, then the firewall will drop packets destined for Transmission Control Protocol (TCP) port number 23, the port where a Telnet server application would be listening.
Packet-filtering firewalls are available into two categories: stateful and stateless. Stateless firewalls examine packets independently of one another and lack context, making them easy targets for hackers. In contrast, stateful firewalls remember information about previous packets and are consider much more secure.
Next-Generation Firewalls (NGFW)
NGFW combines traditional firewall technology with additional functionality, such as encrypted traffic inspection, intrusion prevention systems, anti-virus, and more. It includes a Deep Packet Inspection (DPI). While basic firewalls only look at packet headers, DPI examines the data within the packet itself. It enables users to more effectively identify, categorize, or stop packets with malicious data.
The benefit of a NGFW is that it combines the strengths of each type cover each type’s weakness. It is often a bundle of technologies under one name as opposed to a single component. A Modern network have too many entry points and different types of users that have stronger access control. Therefore, security at host is necessary. This need for a multilayer approach has led to the emergence of NGFWs.
A NGFW integrates three key assets: traditional firewall capabilities, application awareness, and an IPS. NGFWs also bring additional context to the firewall’s decision-making process.
Proxy Firewalls
A proxy firewall serves as the gateway from one network to another network for a specific application. Proxy servers can provide additional functionality such as content caching and security by preventing direct connections from outside the network. However, this also may impact capabilities and the applications which they can support.
Proxy firewalls filter network traffic at the application level. Unlike other firewalls, the proxy acts as an intermediary between two end systems. The client must send a request to the firewall, where it evaluates against a set of security rules and then permitted or blocked. The proxy firewalls monitor traffic for layer 7 protocols such as HTTP and FTP and use both stateful and DPI to detect malicious traffic.
Network Address Translation Firewalls (NAT)
NAT allows multiple devices with independent network addresses to connect to the internet using a constant IP address, keeping your IP addresses hidden. As a result, attackers scan a network for IP addresses but cannot capture details, providing higher security against different attacks. NAT firewalls are identifiable to proxy firewalls in that they act as an intermediate between a group of computers and outside network traffic.
Stateful Multilayer Inspection Firewall (SMLI)
SMLI filter packets at the network, transport, and application layers, checking them against known trusted packets. Like NGFW firewalls, SMLI also examines the entire packet and only allow to pass if they pass each layer individually. They are checked at each layer separately. These firewalls examine packets to determine the state of the communication to ensure all communication is only taking place with trusted sources.
Unified Threat Management Firewall (UTM)
A UTM device typically combines, in a loosely coupled way. The functions of a stateful inspection firewall with intrusion prevention and antivirus. The intrusion prevention system prevents any intruder from attacking the system. While Antivirus protects the system from viruses and worms. It may also include additional services and often cloud management. UTMs focus on simplicity and ease of use.
Difference between Traditional Firewall and Next-Generation Firewall
| Traditional Firewall | Next-Generation Firewall |
| The traditional firewall mainly provides stateful inspection of incoming and outgoing network traffic that entering or exiting points inside the network. | Next Generation firewall provides stateful inspection of incoming and outgoing network traffic that entering or exiting point inside network along with many additional features. |
| It provides partial application visibility. | It provides full application visibility. |
| Based on the old firewall system. | Based on a modern firewall system with advanced features. |
| The traditional firewall works on layer 2 to layer 4. | Next-Generation Firewall works on layer 2 to layer 7. |
| It does not support application awareness. | It supports application awareness. |
| Integrated Intrusion Protection System and Intrusion Detection System are deployed separately. | Integrated Intrusion Protection System and Intrusion Detection System comes with it. |
Zone-based firewall
A firewall is a network security system that monitors and takes actions on the ingoing or outgoing packets based on the defined rules. It can be a hardware device or software device. An organization that cannot afford a hardware firewall device uses an alternative i.e implementing firewall features on the Cisco IOS router by using CBAC or by using a Zone-based firewall. CBAC is a predecessor to a Zone-based firewall.
A Zone-based firewall is an advanced method of the stateful firewalls. In a stateful firewall, a stateful database is maintained in which source IP address, destination IP address, source port number, destination port number is recorded. Due to this, only the replies are allowed i.e if the traffic is Generated from inside the network then only the replies coming from outside the network are allowed.
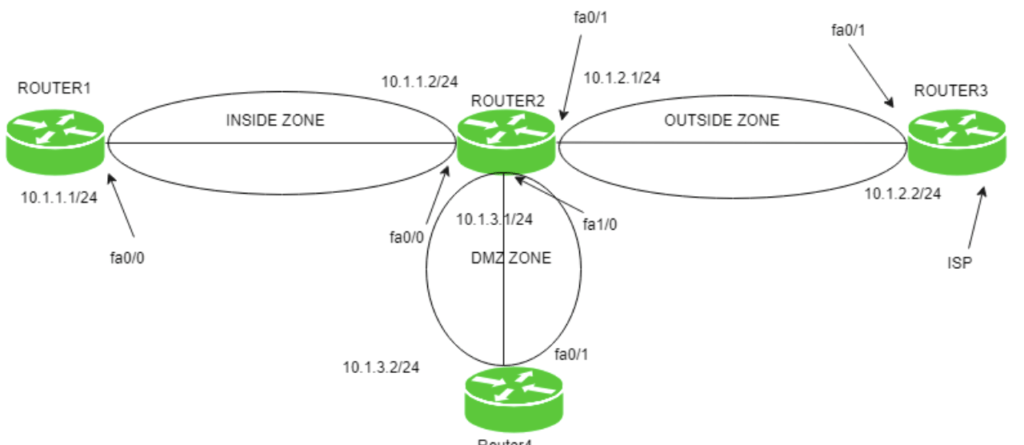
Working of Zone-based firewall
The first step is to define the zones and name them. Although, we can give any name by naming convention that makes sense, name the zones as inside, outside, and DMZ.
Inside: The most trusted network. It is basically a private network. Outside: The most untrusted network. It is a public network. DMZ: contains devices like servers. It defines the public zone.
Since zones have been named, policies are created which will include what type of traffic is allowed to be generated and allowed to go through from inside network to outside network and what actions should be taken on the traffic.
The actions can be as follows:
- inspect: an entry will be made in stateful database for the protocols (for which the policies has been applied) so that the replies (for inside network) can come back.
- drop: default action if the traffic does not match the policies.
- pass: the traffic will be allowed from one zone to another but no session is maintained.
If the traffic does not match the policy then we will drop it due to the default policy. These policies will define in one direction in a zone pair. If conditions require to allow initial traffic to generate in both directions, then creations two separate zone-pairs takes place.
Advantages of Zone-based Firewall
- By default, the traffic blocking takes place, unlike CBAC.
- Unlike CBAC, a Zone-based firewall is no heavily dependent on ACL.
- It is easy to add another interface as only the zone has to be declared to which the interface belongs as all the policies will be the same as applied explicitly before for that zone.
- In a Zone-based firewall, no traffic has access from one zone to another while in CBAC, all traffic has access if no explicit ACL is present.
AWS Firewall
Amazon Web Services (AWS) is a public cloud service platform that supports a broad section of operating systems, programming languages, frameworks, tools, databases, and devices. AWS uses a shared security model. It means that while Amazon takes responsibility for protecting the infrastructure that runs AWS services, the customer is responsible for the data and applications utilized by end-users. It is important that customers take the necessary steps to protect their data, applications, and networks by securing their digital property with a firewall of some type.
The term AWS Firewall refers to any computer security system that monitors the traffic, network, applications, or data running on the Amazon cloud. Generally, these security systems fall into two categories.
AWS web application firewalls
Web Application Firewalls play a critical role in the protection of web-based applications running on the Amazon cloud. They form the backbone for defensive against cloud-based exploits that compromise security or harm the availability of applications and data. There are numerous companies that offer Web Application Firewalls on the AWS marketplace, each with their own advantages and disadvantages. While each AWS WAF differs in technology and implementation, the most generally provided:
- Application Security: Protecting web applications is any Web Application Firewall’s primary purpose. A powerful WAF should be able to protect applications, data, APIs, and mobile app backends from common cyber attacks such as OWASP Top 10, zero-day threats, data leakage, and DDoS attacks.
- Traffic Filtering: Traffic filtering is one of the most practical and important operations performed by a Web Application Firewall. By filtering traffic based on factors such as HTTP headers, keywords, IP addresses, and even URI strings, the Web Application Firewall can prevent harmful interactions before they reach an application.
With AWS maintaining its place as the most popular public cloud infrastructure platform, comprising above 40% of applications workloads in the public cloud, applications utilizing Amazon infrastructure are often under attack. It is important that companies and individuals invest in the security of their applications and data with a powerful and proven WAF.
AWS Network Firewalls
Network Firewalls on AWS offer network protection that add up the application protection provided by Web Application Firewalls. While there is some overlap between what a Network Firewall and Web Application Firewall protect, Network Firewalls provide security over the entire network which includes the high vulnerable port and protocol levels.
Some powerful security features.
- Packet Filtering: By monitoring all incoming and outgoing packets the firewall can regulate which applications and hosts are allowed to interact with the network.
- Virtual Private Network (VPN): Many modern firewalls offer VPN technology to allow virtual point-to-point links between two nodes through a safe and regulated source.
- Deep Packet Inspection (DPI): DPI is a method that inspects not only the packet’s multiple headers but also the actual data content of the packet. In this way, the firewall can filter protocol non-compliance, viruses, spam, intrusions, or other defined criteria.
- Antivirus Inspection: Antivirus inspection checks packets for the virus that travels through the network to infect endpoint devices.
- Website Filtering: Website filtering is a technique that uses to check incoming web pages to see if the page needs to censor or declined to show at all. Reasons for blockage could be advertising, pornographic content, spyware, viruses, and other unsafe content.
- DNS Reputation Filtering: By filtering content against a database that records the reputation and validity of an IP address, firewalls can block harmful content more easily.
Currently, AWS does not offer its own Network Firewall, therefore customers must rely on third-party companies for network protection on their AWS deployments. However, It is important to consider the vulnerability of your data and application-related-packets on their way to and in retrieval from the cloud. In both these cases, a Web Application Firewall is not enough to guarantee their protection. Often hackers will try and steal data or information on its way out of an AWS Network and into a private network. As companies continue to spread their online resources across multiple clouds and infrastructures the opportunity for cybercriminals to strike continues to grow.